Zeroday for WordPress plugin
- Blog
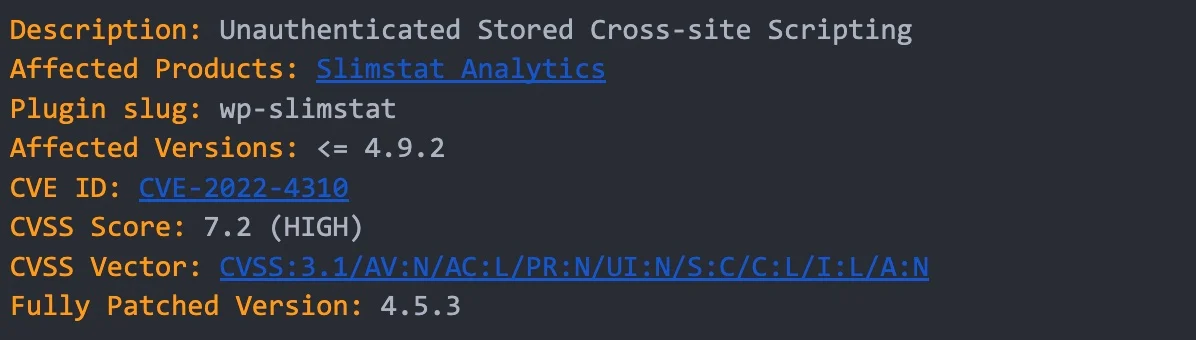
High Severity Vulnerability in Slimstats Analytics WordPress Plugin Affects 100,000 Active Users (CVE-2022-4310)
Introduction
On Dec 06, 2022, during an internal research project, a high severity vulnerability present in the Slimstat Analytics WordPress plugin was discovered. This vulnerability allowed unauthenticated attackers to inject arbitrary web scripts in pages that will execute whenever an administrator user views the logs.
We initially contacted VeronaLabs on Dec 06, 2022, via WPScan responsible disclosure program and provided all the necessary details, including a proof of concept. The WPScan team confirmed the vulnerability on the same day and reached out to VeronaLabs. On Dec 12, 2022, The VeronaLabs team fixed the vulnerability, a patch was released in version 4.9.3 and the WPScan team scheduled a disclosure date.
This is considered a high-severity security issue that could lead to the execution of malicious code on a vulnerable site. If you haven’t updated yet and are running Slimstat Analytics version 4.9.2 and below, we highly recommend that you update to version 4.9.3 immediately.
Slimstat Analytics is used for tracking returning customers and registered users, monitor Javascript events, detect intrusions, and analyse email campaigns. As part of its functionality, it allows an administrator user to view the logs of users' requests on the site. However, due to a lack of proper input validation and output escaping, it has been discovered that it's possible to inject malicious Javascript and HTML code into the logs. When an administrator views these logs, the malicious code will be executed, posing a significant security risk.
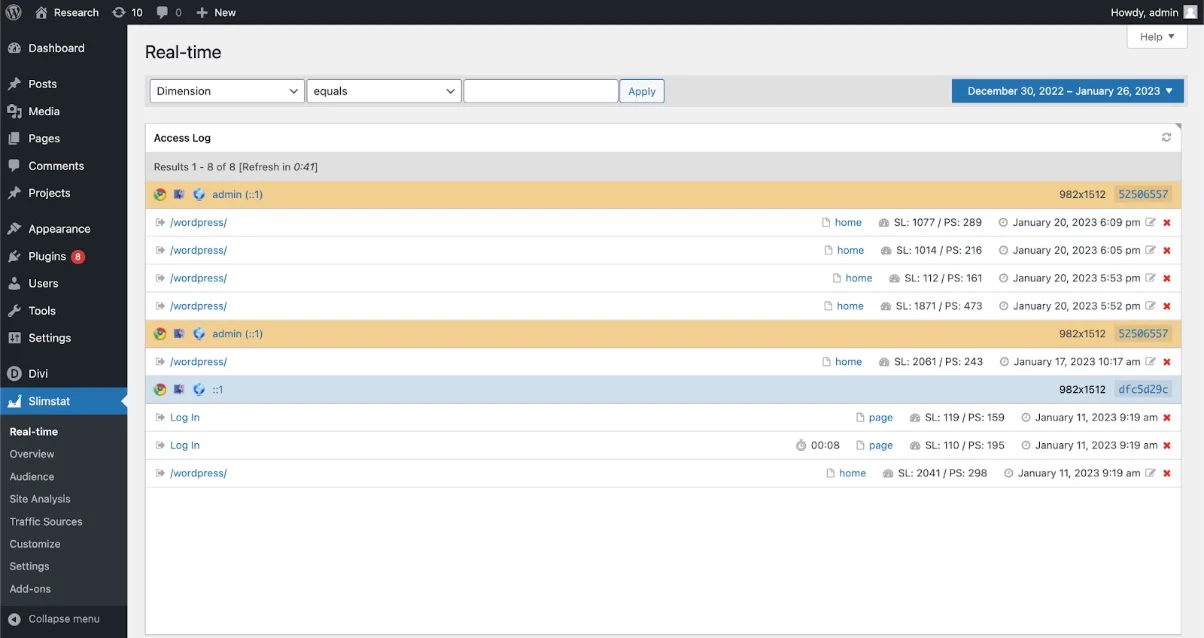
What caused the vulnerability
When taking a closer look at the function source code, we can see that the access log is taking unsanitised input from multiple variables such as REQUEST_URI and RESOURCE and outputting them without any escaping resulting in the cross-site scripting issue.
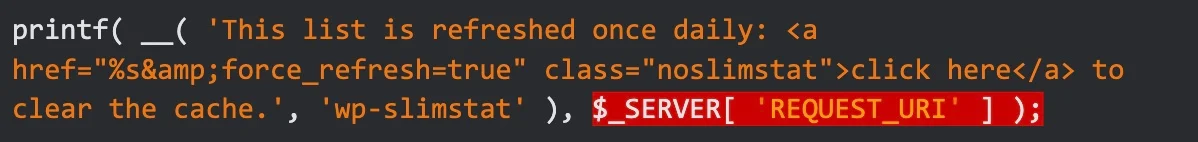
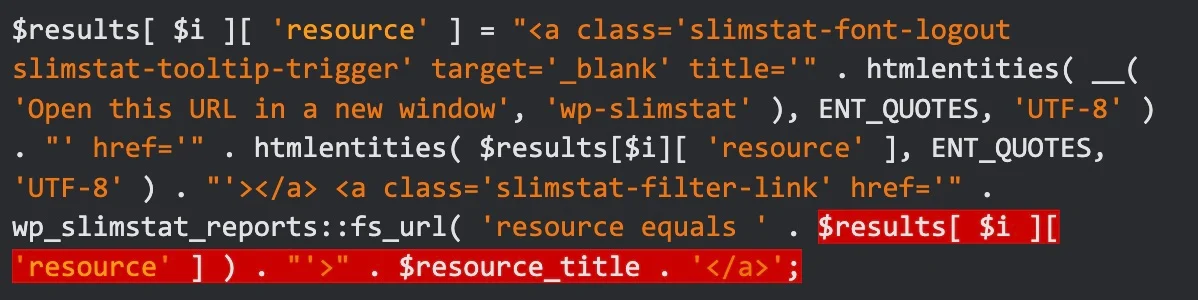
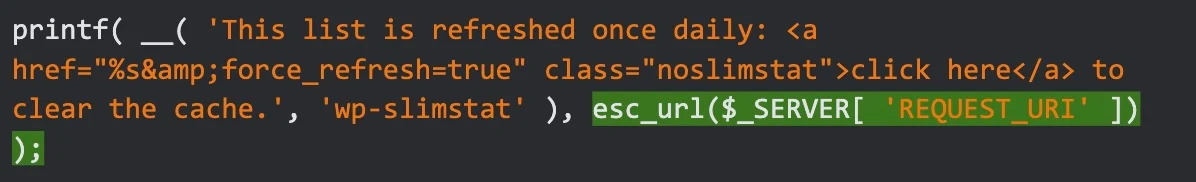
Fortunately, VeronaLabs was very quick to respond and release a patch that escapes every URL input variable before storing it in any function.
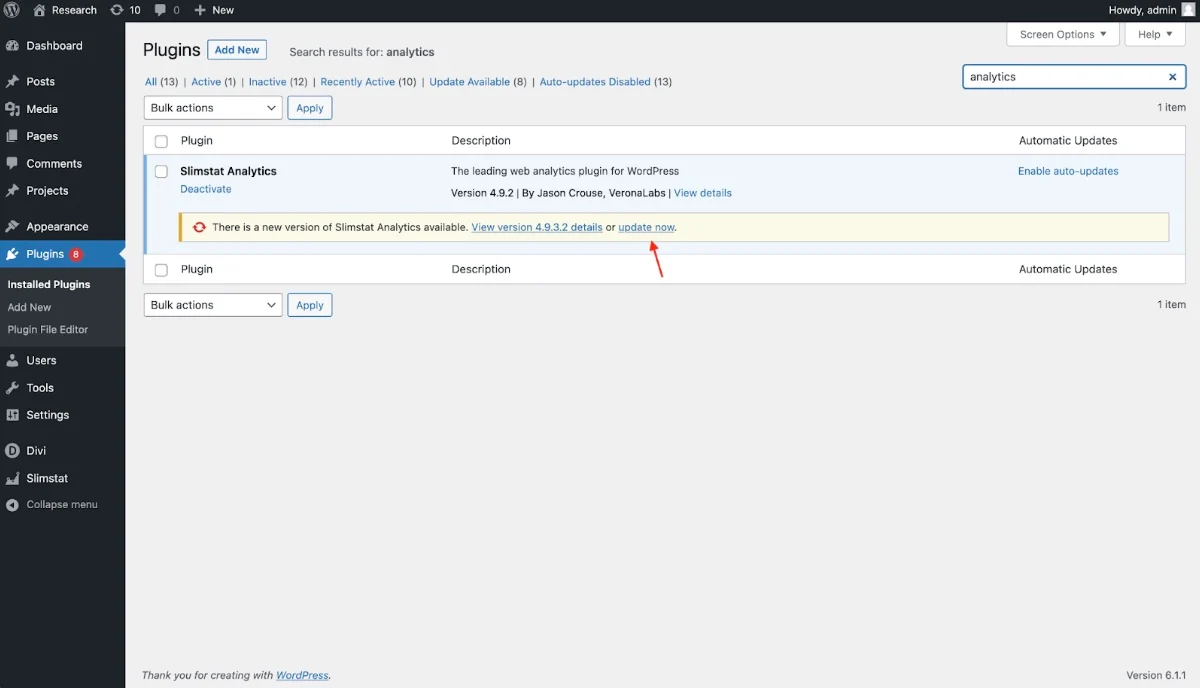
How to update Slimstats Analytics?
Updating the Slimstats Analytics plugin is a simple process. Log in to your WordPress dashboard and go to the plugins section. Look for the Slimstats Analytics plugin, and you will notice an alert that an update is available. Click the “Update Now” button to begin the update process.
Proof of Concept
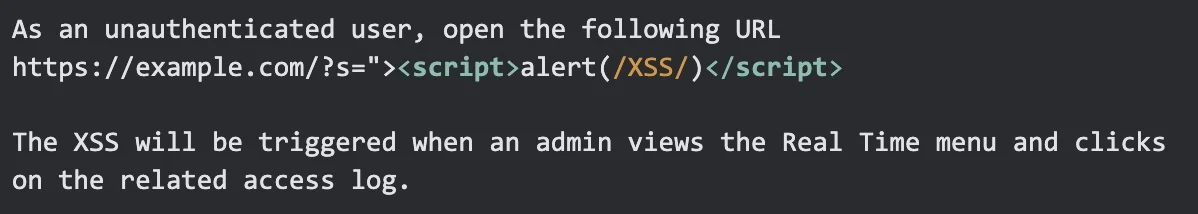
Due to the high severity of the vulnerability and high user install base, the proof of concept of this vulnerability was pushed to be released on January 09, 2023, to give users time to update. Below is a simple proof of concept for the vulnerability.
Bonus for bug bounty hunters
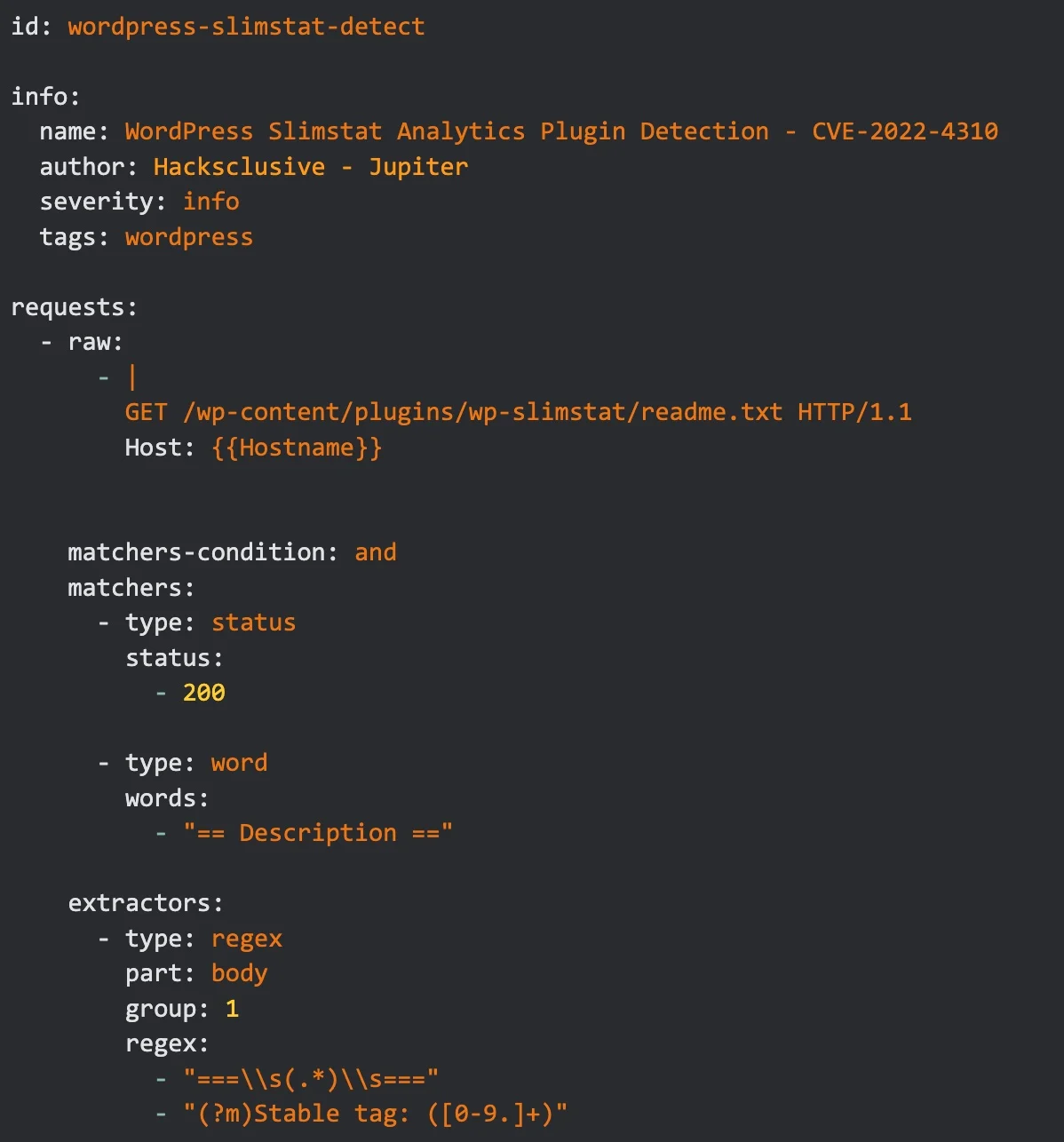
To contribute to the community, we have created a Nuclei template to efficiently identify instances of WordPress sites using this plugin on a large scale. However, it is important to only use this template on targets you have been authorised to test.
The template is designed to determine whether the target website has the Slimstats Analytics plugin installed and, if so, which version is currently in use.
Timeline
- Dec 06, 2022 - Initial discovery of the vulnerability and initial vendor contact via WPScan responsible disclosure program.
- Dec 06, 2022 - WPScan team confirmed the vulnerability and Contacted the vendor.
- Dec 12, 2022 - Vendor confirmed the vulnerability and started working on a patch.
- Dec 12, 2022 - Patch was released, and the WPScan team confirmed the fix and scheduled a full disclosure date.
- Dec 15, 2022 - WPScan team fully disclosed the vulnerability and a proof of concept release date was scheduled.
- Jan 09, 2023 - WPscan team released a proof of concept of the vulnerability.
Conclusion
In summary, a high-severity vulnerability was discovered in the Slimstat Analytics WordPress plugin on December 06, 2022. This vulnerability allows unauthenticated attackers to inject arbitrary web scripts into the logs that will execute whenever an administrator user views them. The vulnerability was reported to the plugin developer, VeronaLabs, and a patch was released on December 12, 2022, in version 4.9.3. Users who have not yet updated to this version are highly recommended to do so as soon as possible.
A Special thanks to the WPScan and Slimstats Analytics teams for working with us to quickly resolve this issue and protect Slimstats Analytics users.

Get in touch
with us today!
We will get back to you as soon as possible! If instead, you want to meet us, let us know where and when, and we'll be there!